Running a node
Monitoring your node
NIS listens on port 7890, so a first way to monitor your node is to check that your server listens on that port. As an example we will configure UptimeRobot to monitor that port. This should give you the required information to configure any other monitoring solution.
It is possible to get information from a running nis by sending HTTP requests. Several URLS are handled.
Status URLs will give JSON-formatted answers, and their meaning is detaild in the NIS API documentation.
Node URLs will give information on the node, such as the version that it is running.
Status URL /heartbeat
You configure your monitoring solution to send requests to the url http://YOUR_IP:7890/heartbeat. A NIS instance
receiving this request will answer if the node is up and able to answer to requests.
In UptimRobot, the form configuring a new monitor hence looks like this:
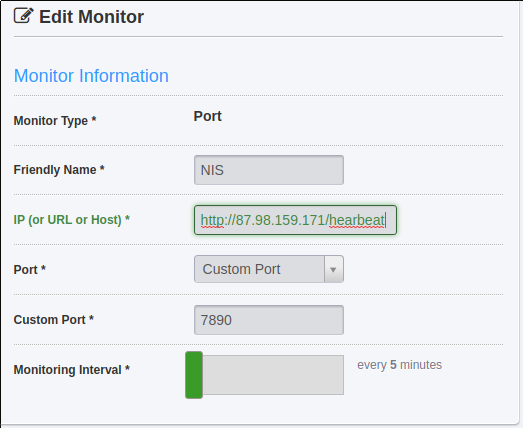
UptimeRobot Monitor definition
Status URL /status
The URL /status of your node returns a small JSON object giving some info on your node’s status.
Check the NIS API documentation linked above for its meaning.
Status URL /node/info
A request sent to that URL gets a JSON-formatted response, giving basic information on the node, such as its version and the network it is running on (mainnet, testnet)
$ http http://104.238.161.61:7890/node/infoGET /node/info HTTP/1.1 Accept: */* Accept-Encoding: gzip, deflate Connection: keep-alive Host: 104.238.161.61:7890 User-Agent: HTTPie/0.9.8 HTTP/1.1 200 OK Access-Control-Allow-Headers: Content-Type Access-Control-Allow-Origin: * Content-Encoding: gzip Content-Type: application/json Server: Jetty(9.2.11.v20150529) Transfer-Encoding: chunked Vary: Accept-Encoding, User-Agent { "endpoint": { "host": "104.238.161.61", "port": 7890, "protocol": "http" }, "identity": { "name": "Hi, I am Alice7", "public-key": "64f0c867c52e8d3f7fe478854dbb197646d06041cc16b56595c03a217af6564b" }, "metaData": { "application": null,